By Andreja Jarc.
Synchronized timing is vitally important when many systems work together in a network. Services such as Logfiles, Correlation of Events, User Authentication Mechanisms, Job Scheduling e.g. for backups or Active Directories running on distributed platforms use accurate timestamps to record events in chronological order and to avoid conflicts with data replication. Without accurate time synchronization these services cannot operate.
As is true for other network services, time synchronization is exposed to numerous cyber vulnerabilities such as hacker attempts and security hazards. Spoofing or falsifying of time information may severely influence the operation of time-critical applications and degrade stability of networks.
Meinberg therefore dedicates special care and attention to safety and security procedures which are implemented and regularly upgraded on LANTIME NTP servers to protect the time service from undesired attacks and keep synchronization operating properly.
In this post I will introduce you to some efficient safeguards available in LANTIME Generation 6 Servers which can protect against the vulnerability threats and reduce risks to an acceptable level.
Access Control and User Management
It is possible to create multiple user accounts on a LANTIME system; each account can be assigned to one of three user privilege levels:
• Super-User full read / write control over Web GUI and Command Line functions
• Admin-User restricted read / write control over Web GUI and CLI functions
• Info-User read permission only
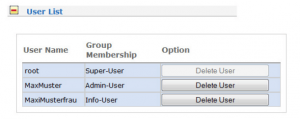
Figure 1: A list of multiple users on a LANTIME with different privileges.
Password Options
All users can be password protected. One can activate special options to enhance security features of the user passwords as follows:
• Minimum password length
• Allowance of secure password only
• List of valid special characters
• User must change the password periodically in provided intervals
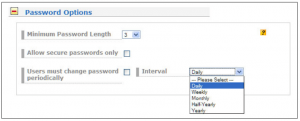
Figure 2: Security levels for password generation.
Activation / Deactivation of unsecured network services
All available Network Services can be activated /deactivated separately for every interface. Therefore any unsecured network protocols such as FTP, HTTP or Telnet can be deactivated respectively. See the following example:
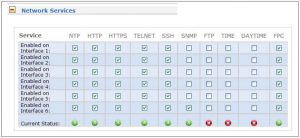
Figure 3: Activation / deactivation of network services for each interface separately.
External authentication via TACACS+ and RADIUS
There are several user account authentication methods available on LANTIME systems. One option is an external authentication with TACACS+ or Radius. TACACS+ by contrast to Radius refers to a family of protocols for remote authentication and network access control where entire packets are encrypted.
TACACS+: Terminal Access Controller Access-Control System (TACACS) is a remote authentication protocol that is used to communicate with an authentication server commonly used in UNIX networks.
RADIUS: Remote Authentication Dial In User Service (RADIUS) is a networking protocol that provides centralized Authentication for MEINBERG Time Servers to connect and use the network services. RADIUS is a client/server protocol that runs in the application layer, using UDP as transport.
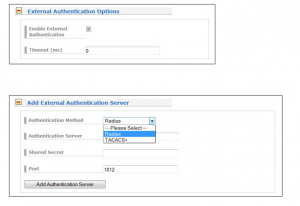
Figure 4: Activation of Remote Authentication in the User Administration dialog.
Client / Server Authentication via Autokeys and Symmetric Keys
NTP Version 4 supports symmetric keys and additionally provides also the Autokey feature. Both supported by Meinberg LANTIME systems.
The authenticity of received time at NTP clients is ensured by the symmetric key technique. By this method every packet is equipped with a 32 bit key ID and a cryptographic 64/128 bit checksum of the packet. This checksum is built with MD5 or DES, both algorithms offer a sufficient protection against data manipulation.
Figure 5: Web GUI dialog for NTP MD5 Keys generation.
Hardware Protection enabled by Redundant Configuration Setups
There are a number of methods to assure highly available and reliable operation of Meinberg LANTIME systems. Different redundant configuration setups enable a time server to operate seamlessly if some of its components experience operational difficulties.
Meinberg LANTIME and IMS (Intelligent Modular Synchronization) systems allow redundant configuration to protect from the following potential failures:
1. Power supply failure
2. Reference clock failure (signal loss or malicious disturbing)
3. Network unavailability
4. Inadequate server performance
5. Physical damage.
More about various redundant configuration setups using LANTIME systems refer to one of the older posts:
https://blog.meinbergglobal.com/2013/11/27/ntp-network-redundancy/
If you wish to learn more on NTP safety and protection measures of the network timing, visit a NTP Complete Training at Meinberg Sync Academy.
More information about NTP Time servers for networks of different sizes and industries you can find at Meinberg website: www.meinbergglobal.com.
Enjoy Your Summer and Stay In Sync with Us!
Hi,
I’m trying to create Tacacs+ on my Cisco ISE server, and I wonder wich attributes i should send return to get the SuperUser role?
Best regards
Claus Jespersen
Hello Claus,
for correct Tacacs+ settings please check our LANTIME manual which you can find here for download: https://www.meinbergglobal.com/download/docs/manuals/english/ltos_6-24.pdf
The Chapter 9.1.8.5 is dedicated to external authentication methods, and Tacacs+ is one of them.
Very good and informative post -as relates to NTP. But what about PTP. It is often seen or implied the two are similar and one can be substituted for the other with the difference being mainly in time accuracy. Does this hold true in the context of Security and Protection?
–Fred Huffman, Huffman Technical Services
PS: So glad to see the use of “Security and Protection”, which I take to mean Security of Timing Signals, and Protection of the network carrying or distributing them.
Thanks in advance for any comments back!
Security is a problem for network timing protocols. PTP currently has only an experimental security mechanism defined in the standard. This mechanism is generally viewed as flawed by PTP community. As a result commercial products which include PTP, don’t implement it.
NTP is better off. It has a built in security mechanism, which is available in the most of the devices, or free software clients. Unfortunately it relies on a MD5, a hashing algorithm which has been broken.
The good news is security is currently being worked on in the standards organizations. The upcoming revision of IEEE 1588 will include an optional authentication TLV, and an infomative annex on securing PTP. The authentication header is not a complete solution for a native security mechanism, since key exchange still needs to be specified. But it’s a start. The NTP security mechanism is being scrapped for a new mechanism, which will include key disribution. Both new standards may get published this year.
— Doug
Hello,
Could you please give me some details about your “secure password” ?
What do you call “secure” ? Minimum length, minimum number of special characters, digits, upper case, … ?
Also, is it possible to change the SSH default port ?
Thanks in advance for your help.
Bilal
In reply to Bilal.
Hello Bilal,
this is an excerpt from our LANTIME V6.24 manual:
An user can configure a minimum password length manually. The configured length will be used every time when a new user is created or when a password shall be changed.
The password must contain at least one lower character [a-z], one upper character [A-Z], one number and one special character.
User must change the password periodically.
The SSH port can not be configured via standard configuration services.
For more information about password security, check our Meinberg manual at: https://www.meinbergglobal.com/download/docs/manuals/english/ltos_6-24.pdf
Hi ,
also about the security aspect, I would like to know the recommendation or best practice about the architecture, does having an antenna on the lantime have to be put on a separate DMZ? FYI, we have frontal & dorsal firewalls, how we can put the lantime, on dorsal FW next to the servers, or in frontal, and open the flox matrix (123 NTP port).
Thak you.
I would say that the best practice with respect to firewalls is to place an ntp server inside the firewall and use GNSS to get the time to the server.
Hello,
When external auth is enabled, is login still possible using the root account, in the event that all external auth servers become unreachable ?
I’ve had a look through the online docs and manual but could not find the answer.
Thanks
I’m not sure what is available for configuration, since the functionality gets expanded with every firmware release. I suggest asking the tech support team at: techsupport@meinberg.de.