Five Minute Facts About Packet Timing
In multicast PTP a slave port need only subscribe to the PTP multicast addresses and timing will come to it. However, in unicast PTP a slave port has to reach out to the master port it wants time from with PTP message requests. It is more of a client-server paradigm. This means that the slave port starts with the unicast addresses of the master port and sends the requests for Announce, Sync and Delay Response messages. Here I am talking about master and slave ports, not clocks, since they might refer to individual ports on a Boundary Clocks.
The question we are looking today is: which master port? There are several approaches to answering this question:
1. The slave port could have the address of just one master port, and it uses that one.
2. The slave port could have a prioritized list of master ports. That way if the first one is unavailable or refuses to grant messages because of capacity management, then the slave port can try its luck with the next one on the list.
3. The slave port can compare the clock quality attributes of several master ports and pick the best one.
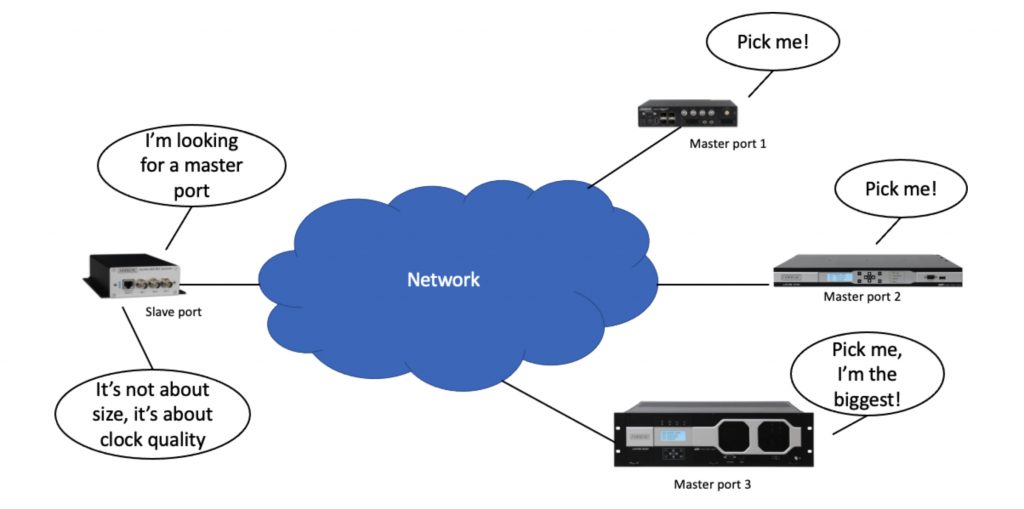
Figure 1. A slave port selects from three master ports in a unicast PTP network
The way this works is that the unicast master can ask for Announce messages from multiple master ports and run the BMCA among them and select the best one. Figure two shows the message sequence. The slave ports sends Announce message requests to each of the master ports, the master ports respond with grant messages and then start sending Announce messages. The slave port examines the Announce message fields and runs the BMCA, to select the one it wants.
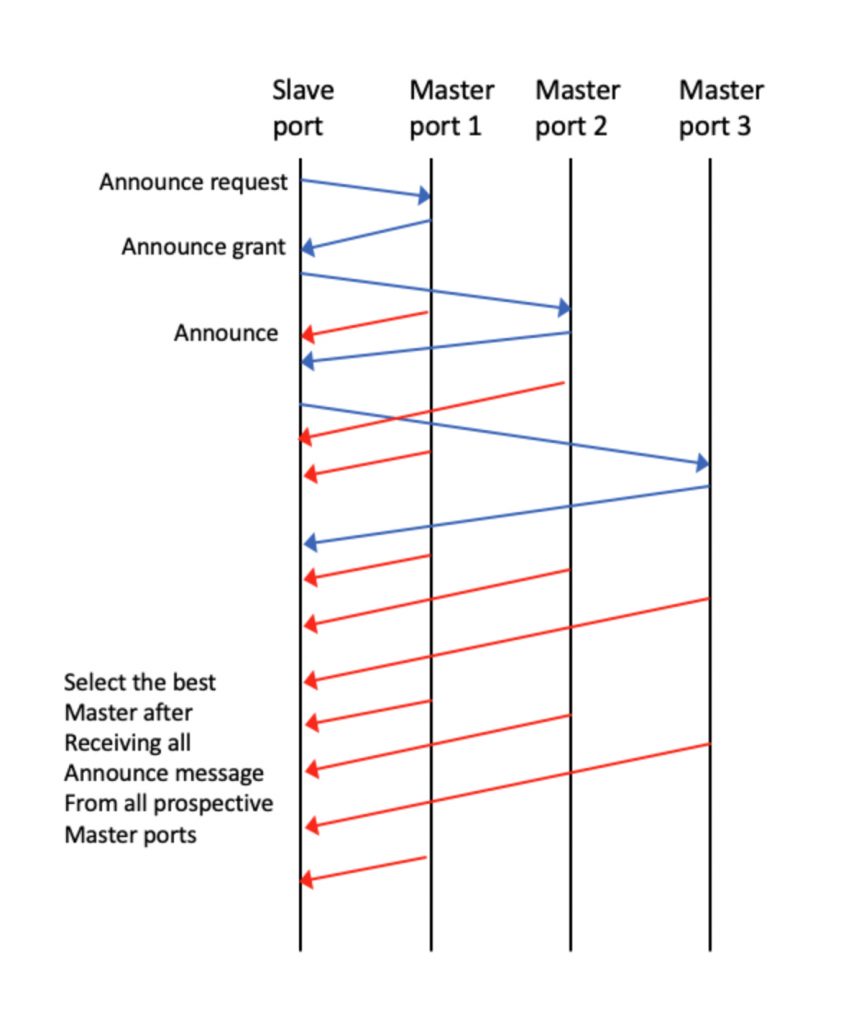
Clock attributes in the Announce messages used in the BMCA can change over time, especially Clock Class, since that reflects the status of the timing refence of the master port, for example is it locked to a GNSS receiver or in holdover. For this reason, the slave port can keep the Announce messages from multiple masters coming all the time, that way it can dump its current master if that port is no longer (clock) classy enough, and switch to the new best master.
If you have any questions about packet timing, don’t hesitate to send me an email at doug.arnold@meinberg-usa.com, or visit our website at www.meinbergglobal.com.
If you enjoyed this post, or have any questions left, feel free to leave a comment or question below.