Five Minute Facts About Packet Timing
By Doug Arnold
What is with al of these TLVs in the Precision Time Protocol?
Let’s start at the beginning, TLV stands for “type, length, value.” It is a general means to extend a PTP message with some extra information for some optional feature or whatever. TLVs are used in many network protocols, not just PTP. A TLV in PTP has the structure: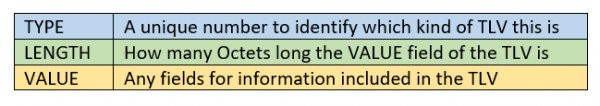 Figure 1: General Structure of a TLV In PTP
Figure 1: General Structure of a TLV In PTP
Let’s look at a simple example from the upcoming revision of PTP. The length of any PTP message can be increased by using a PAD TLV. TLVs are considered so important in 1588 that we type them with all caps! The PAD TLV has this structure:

Figure 2: Structure for the PAD TLV
Wait, why do you ever want to make a PTP message longer? In the case of Peer Delay PTP networks the propagation delay is measured using Pdelay messages, which are 10 octets longer than the Sync message. This can cause an error if the propagation of the Sync message is different than the Pdelay messages. This can happen if, for example, a link between the master and slave ports contain a media converter, which typically has a message length dependent propagation delay.
Another example of a TLV is the PATH TRACE TLV. The Path Trace option is used to map the route of message from a Grandmaster (GM) to Ordinary Clocks acting as slaves. The GM attaches a PATH TRACE TLV to the Announce messages which it transmits. Each Boundary Clock (BC) which receives an Announce message with this TLV adds its clock ID to the TLV and attaches the TLV to all Announce message which it transmits. This allows PTP nodes receiving the Announce messages to see the route which messages from the GM traverse. The PATH TRACE TLV has this structure:
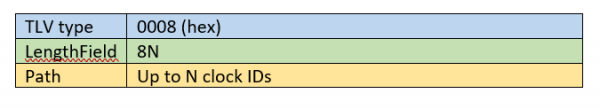
Figure 3: Structure for the PATH TRACE TLV
When a BC receives a TLV on an Announce message and then attaches it, possibly updated, to Announce messages which it transmits, that it referred to as “propagating” the TLV. In IEEE-2008 we called it “forwarding,” but decided to change it to “propagating” in the new edition of 1588 so it would not be confused with the forwarding of frames at the data link layer. Some TLVs are defined as “Non Propagating,” meaning that a BC which receives them does not attach the received TLV to messages which it transmits. An example of this type of TLV is the PAD TLV. All TLVs defined in 1588 are defined as either propagating or non-propagating.
There are many TLVs defined in the standard, including all the native PTP management messages. Too many to list them all here and still meet my promise to you to keep this under 5 minutes. To find out more see clause 14 in IEEE 1588 on TLVs. There are also mechanisms described that allow other standards groups to define profile specific TLVs, and for organizations, such as companies, to define there own TLVs.
If you have any questions about packet timing, don’t hesitate to send me an email at doug.arnold@meinberg-usa.com, or visit our website at www.meinbergglobal.com.
If you enjoyed this post, or have any questions left, feel free to leave a comment or question below.